Deadlines and updates on the latest Common Criteria Version
As a cybersecurity solutions provider, you’re probably aware of all the advantages behind Common Criteria (CC). Besides ensuring product security claims, CC can also help you boost confidence with your end clients and set your product apart from similar, non-certified competitors.
But as cybersecurity improvements move at fleeting speed, the only way to take full advantage of these benefits is to be up to date with the latest CC version.
What effects can the latest ISO/IEC 15408:2022 and ISO/IEC 18045:2022 Common Evaluation Methodology (CEM) revisions have on your product evaluation? Keep reading for insight on the latest procedure implications, transition deadlines, and next steps.
Deadlines and transition period
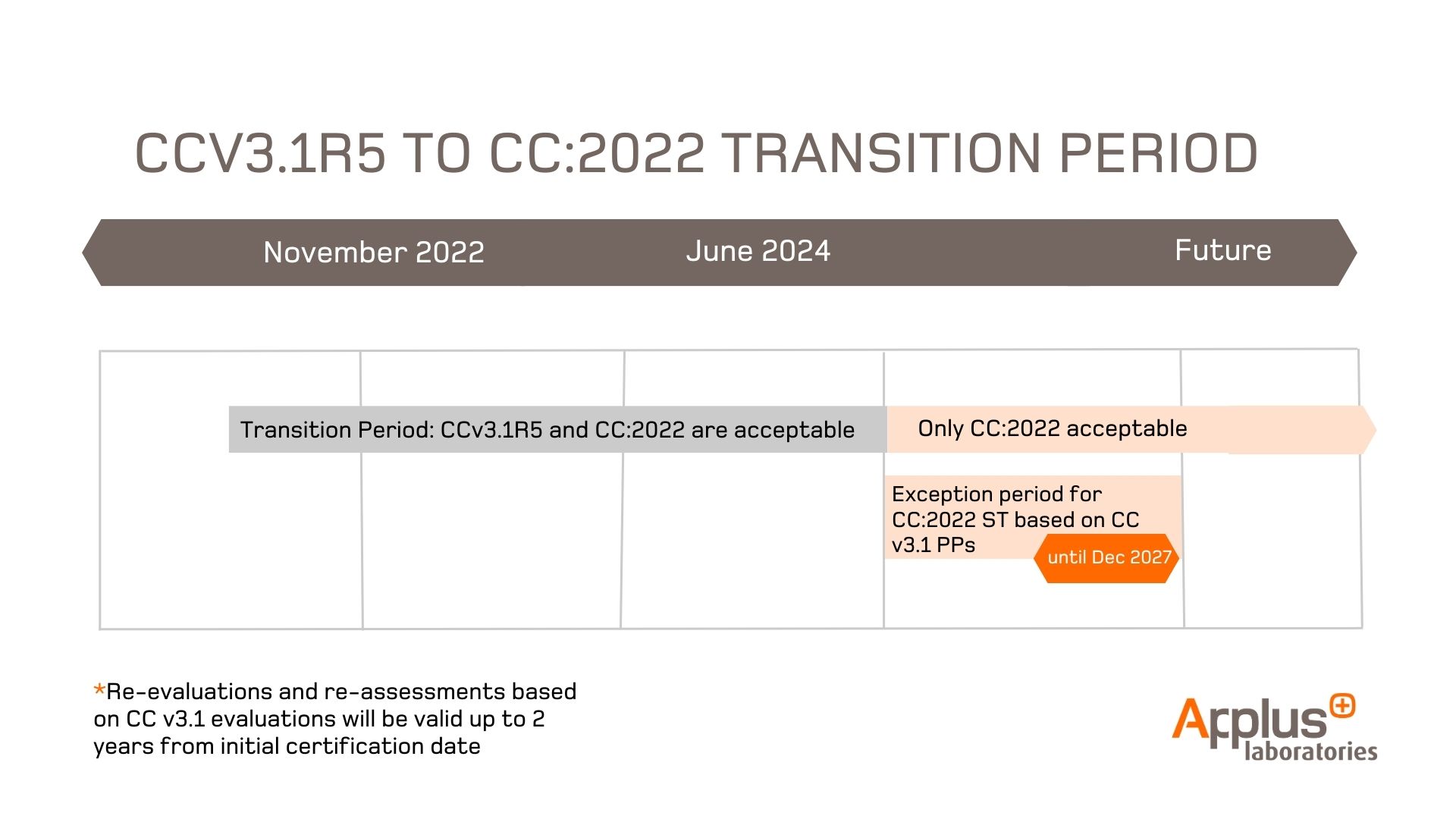
During the ongoing transition period, both CCv3.1R5 and CC:2022 R1 are acceptable, providing clients with the flexibility to choose the version that best suits their needs, for evaluations starting no later than the 30th of June 2024.
However, Security Targets that are conformant to CC:2022, but still based on PPs certified according to CCv3.1R5, will be accepted until the 31st of December 2027.
Finally, after the 30th of June 2024, the re-evaluation and re-assessment assurance continuity activities based on CCv3.1R5 evaluations can be started for up to 2 years from the initial certification date.
CC:2022 standard updates you should know about:
Cybersecurity best practices have evolved since the earlier CCv3.1R5 implementation. But even if ISO/IEC 15408 and ISO/IEC 18045 changes seem considerable, they’re only a mere reflection of how far our cybersecurity expertise has come.
Main take-aways on the new CC:2022 standard:
- Multi-assurance evaluations: Allows heterogeneous products and systems to be assessed by allowing different parts of the TSF to claim different assurance packages, as previously seen, for example, in the Point of Interaction (POI) Protection Profiles (PPs).
- Specification-based approach: Corresponds to the CCRA initiative of low assurance evaluations based on collaborative Protection Profiles (cPPs). The cPPs define custom-made evaluation activities defined at the level of each test or verification task. Allows the use of Direct Rationale PPs, which do not use security objectives for the TOE, but instead directly map Threats and OSPs to the SFRs.
- Composition model changes: Introduces the Network/bi-direction composition model and the Embedded Composition Model, a practice widely used in Smartcards and Similar Devices Technical Domains of SOG-IS, to streamline the composition process. ASE_COMP, ADV_COMP, ALC_COMP, ATE_COMP, and AVA_COMP are introduced as assurance families; the ACO assurance class remains under the name of Layered Composition Model.
- Security Assurance Requirements (SARs) updates: Applies changes to ADV_SPM, and adds the new family ALC_TDA: TOE Development Artifacts, whose objective is to build trust in the development process by ensuring the generation of specific artifacts.
- A revision on Security Functional Requirements (SFRs): incorporates a significant number of SFRs in Part 2, most of which have been widely used for years as Extended Components in PPs and STs.
The CC:2022 standard rethinks its structure:
One of the main changes behind the latest CC:2022 standard is structural. Instead of three parts, it will have five.
- Part 1 and 2: remain the same as in CCv3.1R5.
- Part 3: ISO/IEC 15408-3:2022 encompasses the Security Assurance Requirements (SARs) from the previous version's Part 3.
- Part 4: Includes new aspects to be taken into consideration. ISO/IEC 15408-4:2022 defines a methodology for deriving evaluation methods and activities from ISO/IEC 18045:2022, which can be included in Protection Profiles (PPs) and Security Targets (STs). This additional aspect provides a more flexible and adaptable structure for addressing diverse security evaluation needs.
- Part 5: ISO/IEC 15408-5:2022 contains the Evaluation Assurance Levels (EALs) and the Composed Assurance Packages (CAPs), formerly in Part 3.
Facilitating and speeding up Common Criteria
Our Laboratory is well prepared for handling evaluations and certifications under both CCv3.1R5 and CC:2022 standards. Thanks to this, we can ensure a seamless transition for our clients, providing valuable advice and support to address any concerns or doubts regarding updates.
We are an accredited lab for SOG-IS technical domain’s evaluations up to EAL7, and experts at facilitating and expediting Common Criteria evaluations, thanks to our:
- Innovative framework to automate and speed up certification times.
- Top-notch experts focused on time to market.
- Active contributions to EUCC scheme definition.
- European Commission Support through the SCCG committee.
For further insight and precision into what we do, please stop by our official Cybersecurity Services or get in touch with one of our industry experts.