UNECE WP.29 R155/R156: new cybersecurity regulations for vehicles
As of July 2022, all automotive manufacturers looking to obtain EU type approval for new whole vehicle types must comply with the new WP.29 UN R155/R156 regulations. Then, from July 2024, this requirement will be extended to all new vehicles sold in the EU, regardless of when the manufacturer obtained the type approval for that type of car. Older models still in production might also need to implement changes to comply. In this article, we will talk you through the basics.
Regulatory Framework: UNECE WP.29 UN R155 and R156
The UN R155 and UN R156 regulations have been adopted as official regulations by the UNECE World Forum for Harmonization of Vehicle Regulations (UNECE WP.29), to set a common future framework for vehicle cybersecurity in different parts of the world. UNECE WP.29 cybersecurity regulations officially came into force in January 2021.
UN R155 requires the operation of a certified Cybersecurity Management System (CSMS), while UN R156 requires a Software Update Management System (SUMS) as a future condition of type approval. Together, the UNECE regulations explicitly specify four disciplines:
- Managing cyber risks to vehicles
- Securing vehicles “by design” to mitigate risks further down the supply chain
- Detecting and responding to security incidents across vehicle fleets
- Safely and securely updating vehicle software, including a legal basis for over-the-air updates
As you can see, we are not just talking about a matter of testing for vulnerabilities present in vehicle components. It is much more.
The UNECE WP.29 timeline: where and when
WP.29 applies to the countries that participated in (or now adhere to) the 1958 UNECE Transportation Agreements and Conventions. This group of countries, which includes the nations of the EU, the UK, Japan and South Korea, produced one third of all the world’s vehicles in 2018.
From July 2022, compliance with the new regulations on cybersecurity (UNECE WP.29/R155) will be mandatory to obtain the EU’s Whole Vehicle Type Approval (WVTA). This certificate allows OEMs to sell vehicles that have the same essential elements of the approved prototype throughout the EU, without requiring further testing or certification. If those essential elements are changed in some critical or significant way, a new WVTA is required.
In July 2024, these requirements will be extended to all new vehicles sold in the European Union, including those models that were type-approved before 2022 and that are still in production. Japan and Korea are following similar timelines for vehicles to be sold there.
All manufacturers (including those from the USA and Canada) selling into these markets need to consider the implications of the WP.29 cybersecurity regulations for both their products and processes.
ISO/SAE 21434, a key reference for regulatory compliance
ISO/SAE 21434 is a standard co-developed by the International Organization for Standardization (ISO) and the Society of Automotive Engineers (SAE). ISO SAE 21434 “Road vehicles — Cybersecurity engineering” focuses on cybersecurity risks in the design and development of car electronics.
The WP.29 cybersecurity regulations and ISO/SAE 21434 standard have been developed in parallel to ensure that regulatory requirements can be met by applying existing standards. They are complementary and non-contradictory.
While the regulation is mandatory in some countries and indicates some specific requirements to be met, the standard represents the results of the industry consensus on the key cybersecurity practices that must be followed to achieve relative security throughout the automotive market.
Compliance throughout the vehicle supply chain
The starting point to meet both regulations and comply with the standard is a cybersecurity risk assessment of the vehicle, including all of the integrated components from automotive industry suppliers. Through the so-called TARA (Threat Analysis and Risk Assessment), OEMs will need to prove that appropriate and efficient mitigations have been implemented to reduce the risk of cyberattacks.
OEMs will not be the only stakeholders affected by these new requirements, as Tier 1, Tier 2 and even Tier 3 vendors will also be included in the process of securing a vehicle’s cybersecurity ecosystem. What we are about to face is an integration of new cybersecurity requirements throughout the whole supply chain.
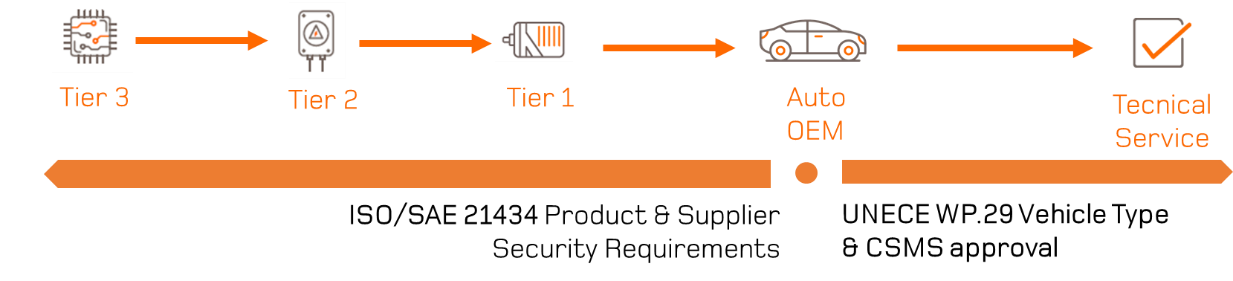
Supporting the automotive supply chain to develop secure components and systems
At Applus+ Laboratories, we have a solid experience in cybersecurity evaluations and penetration testing for a wide range of industries. Our cybersecurity experts can help manufacturers to comply with ISO/SAE 21434 and UN R155/R156, supporting their TARA activities, the evaluation of their risk and threat mitigations, as well as conducting penetration testing when needed.