Everything you need to know about the Spanish ICT Security Products Catalogue (CPSTIC)
Any local or global ICT security product vendor looking to market their products in Spain needs to be aware of the CPSTIC catalogue, especially if they are targeting public bodies or their suppliers.
Applus+ has published this brief guide to help vendors understand what this catalogue is, what its different categories are, and how to certify products to be listed in it.
What is the Catalogue of ICT Security Products (CPSTIC)?
The Catalogue is the list of ICT security products recommended by the Products and Technologies Department of the National Cryptologic Centre, or CCN-PYTEC (Departamento de Productos y Tecnologías del Centro Criptológico Nacional), to be used by the Administration in the protection of its IT assets.
All of the products listed have been evaluated under cybersecurity certification schemes by accredited and independent laboratories—and under the supervision of the CCN—to ensure that they meet the highest security standards.
The catalogue aims to be a reference for the Spanish public sector, and the companies that provide services to it, in the tendering and purchasing of ICT products. For this, the catalogue makes a distinction between two types of products:
QUALIFIED PRODUCTS, which have certified security functionalities and are suitable for use in systems which comply with the Spanish National Security Scheme, or ENS (Esquema Nacional de Seguridad) in the High and Medium categories. Basic category products are not included in the Catalogue.

APPROVED PRODUCTS, which are approved for use in systems managing classified information.
Is inclusion in the Catalogue a compulsory requirement for participating in a public tender?
As of today, the answer is no. However, it is highly recommended, and it will usually be found as a requirement to be considered in the documentation of public tenders.
Therefore, being part of the Catalogue is important if you want to have the same chances of success as other competitors who have already certified and included their products in it. What’s more, in certain circumstances, being quick to get a specific product certified for access to the CPSTIC Catalogue can place the product in a very interesting position for business objectives with the public administration.
If you access the public list of the Catalogue and analyze the different product families and groups, you will see that there are currently certain categories with a very limited offering of qualified or approved products. In some cases, you will even find families that only have one certified solution, or even none at all. This situation undoubtedly gives a competitive advantage to those companies that are pioneers in certifying their product for the Catalogue.
What is the procedure for getting a product included in the Catalogue?
The procedure varies depending on whether the product is to be Approved or Qualified, and in the latter case, it will depend on whether the product needs to comply with the requirements for the ENS Medium Category or ENS High Category.

It should also be noted that the Catalogue is organized by product families. It is orgnised like this in order to categorize the products that form part of the security architecture of ICT systems, i.e., any product that contributes to the system’s operation by implementing functionalities to increase its security level in some of its dimensions like availability, integrity, confidentiality, authenticity and traceability. Each of these families has an assigned reference group in which you can find the required security functionalities, as defined by the CCN.
How do you qualify a product (as a Medium or High Category Qualified Product) for inclusion in the Catalogue?
In regard to Qualified Products, each one that wants to be included in the CPSTIC must have a functional certification, which complies with the Fundamental Security Requirements (RFS) corresponding to its family, as defined by the CCN.
The ENS Category determines which type of functional certification needs to be passed. The LINCE certification provides access to the ENS Medium Category, while the Common Criteria certification provides access to the ENS High Category. Any Common Criteria certifications previously obtained which do not comply with all the RFS defined by the CCN for its product family have to undergo a complementary evaluation of these requirement or, in the worst case scenario, a Common Criteria recertification. Products that do comply with all RFS are also be required to perform a risk analysis. In all cases, validation of the product’s cryptographic algorithms is required.
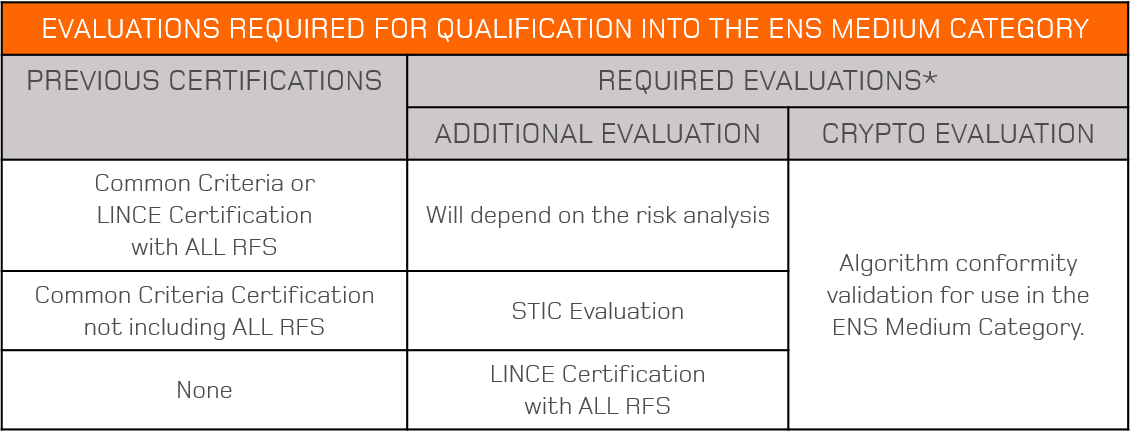
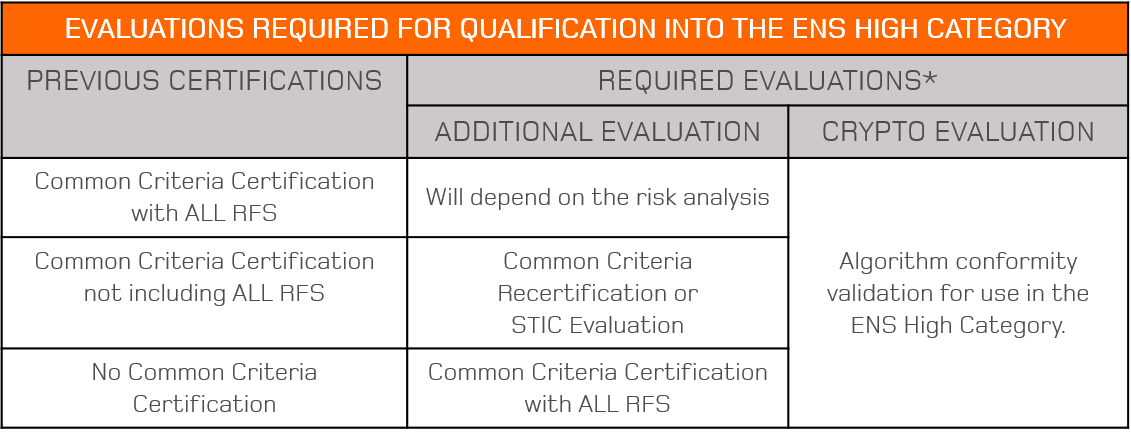
*Except in special cases
How do you approve a product (as an Approved Product with Classified Information) for inclusion in the Catalogue?
IT product which aim to handle classified information must get approval from the CCN. This approval process is not predefined and will depend in each case on the specific product and the information it manages.
The CCN is in charge of deciding what kind of certifications the product requires. While Common Criteria certification and cryptologic certification are often used, other certifications like Tempest, oriented to the evaluation of unintentional emanations, are common too.
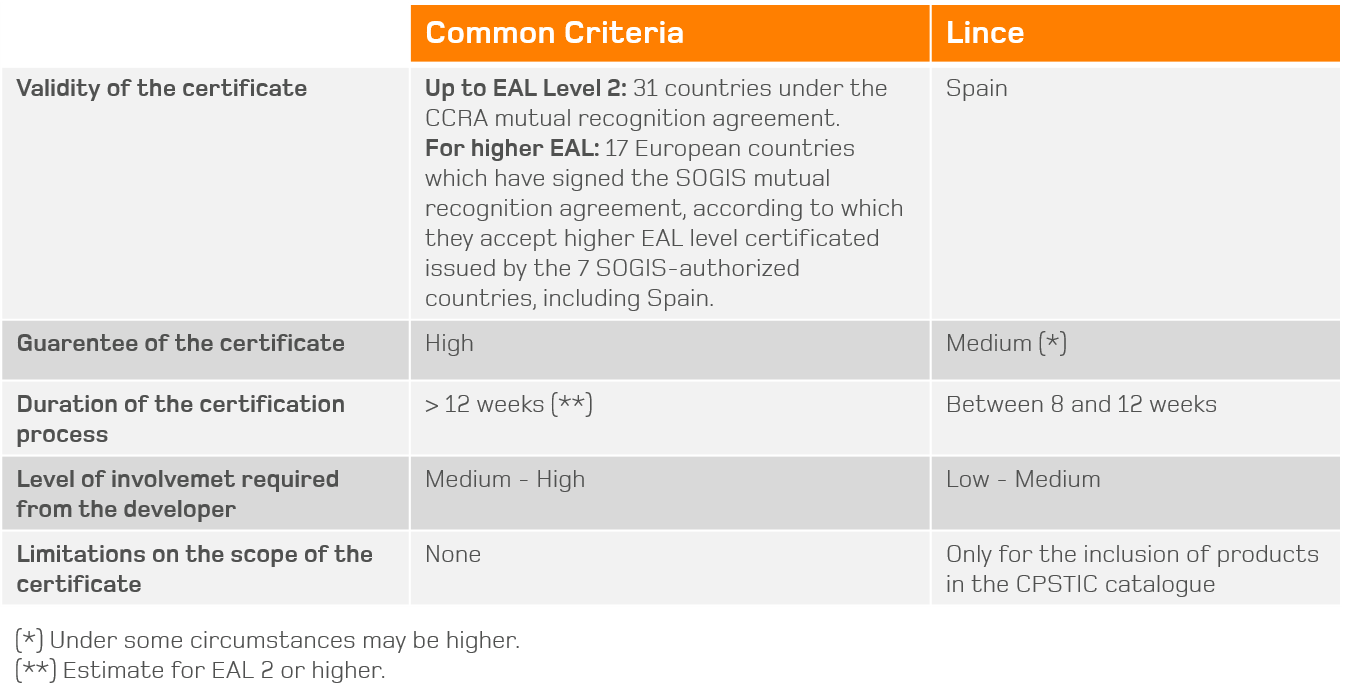
What is Common Criteria certification and how do I achieve it?


Applus+ Laboratories has two labs, which are accredited by the Spanish national certification body, the CCN, to perform both Common Criteria/SOGIS security evaluations (up to EAL 6+).
Click here for more information on Common Criteria certification.
What is LINCE certification and how do I achieve it?

The CCN acts as the certification body for the LINCE scheme, which certifies that a product has successfully passed a CCN-authorized security evaluation. This certification enables the product to be included in the Spanish STIC Product Catalogue.
The evaluation has the following requirements:
- It must analyze the extent to which the product complies with the fundamental security requirements defined in the guidelines [CCN-STIC-140]
- It must measure the resilience of the product’s security functions
- It must be orientated towards vulnerability analysis and penetration testing
- It must be carried out within a predefined timeframe and with a predefined workload
Click here for more information on LINCE certification.
What are the main differences between Common Criteria and LINCE
List of the products in the CPSTIC Catalogue
The list is public and you can find it on the OC-CCN website. We recommend checking the catalogue page regularly for new products in the process of being included, and to evaluate the positioning of your own products compared to the others on the market. Below is a table with the different product families, which can be used as a point of reference when deciding where to include a specific product.
This table provides access to the Fundamental Security Requirements, or RFS (Requisitos Fundamentales de Seguridad) published in annex form:
| CATEGORIES | FAMILIES | ANNEXES (RFS) | ||
|---|---|---|---|---|
| ENS HIGH | ENS MEDIUM | |||
| Control of access | Network Access Control (NAC) | A.1 | ||
| Biometric Devices | A.2 | |||
| Single Sign-On Devices | A.3 | |||
| Authentication Servers | A.4 | |||
| Privileged Access Management (PAM) | A.6 | A.6M | ||
| Identity Management (IM) | A.7 | A.7M | ||
| Operational Security | Anti-virus/EPP (Endpoint Protection Platform) | B.1 | B.1M | |
| EDR (Endpoint Detection and Response) | B.2 | B.2M | ||
| Network Management Tools | B.3 | B.3M | ||
| System Upgrade Tools | B.4 | |||
| Navigation Filtering Tools | B.5 | B.5M | ||
| Security Information and Event Management (SIEM) | B.6 | B.6M | ||
| Mobile Device Management Tools (MDM) | B.8 | N/A | ||
| Other Tools | N/A | N/A | ||
| Security Monitoring | Intrusion Protection and Prevention Devices | C.1 | C.1M | |
| Honeypot / Honeynet Systems | C.2 | |||
| Traffic Capture, Monitoring and Analysis | C.3 | |||
| Sandbox Tools | C.4M | |||
| Communications Protection | Routers | D.1 | D.1M | |
| Switches | D.2 | D.2M | ||
| Firewalls | D.3 | |||
| Proxies | D.4 | D.4M | ||
| Wireless Network Devices | D.5 | D.5M | ||
| Secure Data Exchange Gateways | D.6 | N/A | ||
| Data Diodes | D.7 | N/A | ||
| Virtual Private Networks | IPSec | D.8A | N/A | |
| SSL | D.8B | N/A | ||
| Tools for Secure Mobile Communications | D.9 | |||
| Web Application Firewall (WAF) | D.10 | |||
| Protection of Information and Information Media | Encrypted Data Storage | E.1 | ||
| Offline Encryption | E.2 | |||
| Secure Deletion Tools | E.3 | |||
| Systems for preventing Data Leaks | E.4 | |||
| Electronic Signature Tools | E.5 | N/A | ||
| Protection of Equipment and Services | Mobile Devices | F.1 | N/A | |
| Operating Systems | F.2 | N/A | ||
| Anti-spam | F.3 | |||
| Smartcards | F.4 | N/A | ||
| Back-ups | F.5 | |||
| Reliable Platforms | F.6 | |||
| Virtualization | F.7 | N/A | ||
| Load Balancers | F.8 | F.8M | ||
| CASB Tools | F.9 | |||
| Hyper convergence | F.10 | F.10M | ||
| Video Identification Tools | F.11 | F.11M | ||
| Cloud Services | Cloud Services | G | ||
Applus+ Laboratories: Experts in Cybersecurity Evaluations
Our various IT laboratories have all the required resources and accreditations for evaluating cybersecurity, as well as extensive, proven experience in security assessments and certification processes. For more information on the optimal route for your product to be included in the ICT security product catalogue, get in touch with our experts.