IT security laboratories collaborate with the semiconductor industry to evaluate Integrated Circuit (IC) security against the latest-known attack techniques. To help assess the resilience of ICT products against penetration attacks, cyber-security experts join forces with leading technology companies to develop new testing standards and certification schemes across industry working groups.
Laboratories invest in R&D activities to gain the technical knowledge necessary to understand the hacking methods used in new software and hardware attacks; and in some instances, even detect possible weak points that hackers could exploit in the future.
Applus+ Laboratories is one of the leading companies in chip security evaluations, taking part in several working groups, and our labs are accredited to evaluate the security of IT products using the most stringent methodologies. This year our team of experts developed a new methodology to attack secure Integrated Circuits (IC), which we are now presenting in different industry forums.
The technique was first conceptualised and then validated within our R&D programme, and the developments are based on a reworking of a well-known hardware attack technique – the Fault Injection. In this post, we describe what these kinds of attacks are; how the different techniques are performed; explore the actual limitations of the attacks due to technological changes in chip design and implemented countermeasures; and finally, we will present the new technique discovered by our team to exploit this penetration attack.
Techniques in hardware Fault Injection attacks
Fault Injection is one of the most efficient techniques to attack ICT products. It is designed to hack an IT product by provoking a malfunction, and it can be implemented both as a software attack and as a hardware attack.
This article focuses on the hardware version of this attack, which consist of actively manipulating the chip`s internal functions to cause a fault during the execution of a process. By inducing a fault, an attacker can bypass a security process (such as authentication) or corrupt the data used to enforce the security process. Once a chip`s security has been compromised, the attackers can gain access to sensitive assets managed by and stored inside the chip.
This hardware attack can surpass many types of software countermeasures, but to perform it, the hacker must gain physical access to the chip to induce the fault. The access can be more or less invasive depending on the technique used. There are four different techniques to perform a Fault Injection attack, and each one requires access to different elements of the chip.
Typical countermeasures to hardware Fault Injection attacks
The most common countermeasures against these types of attacks for hardware are passive and active shields to protect the chip against physical access and manipulation. Most chips also include a number of sensors to detect anomalies in temperature, voltage, light or clock frequency.
These countermeasures are now widely implemented in a chip’s security design, which is of direct benefit to security certification widespread within the industry. As a consequence, the effectiveness of glitch attacks has drastically diminished, leaving EMFI, BBI, and especially LFI, as the most common techniques to induce faults in the modern, secure ICs.
Laser Fault Injection attacks: the most effective technique
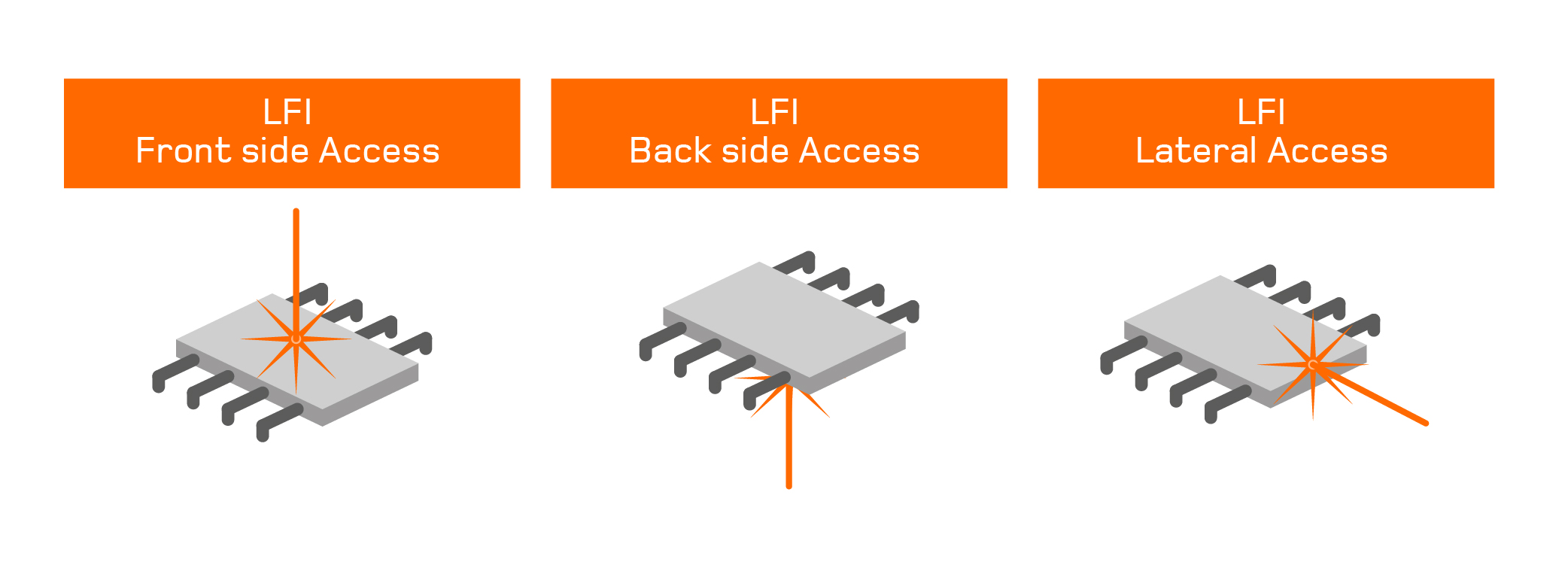
Laser Fault Injection (LFI) is considered to be the most efficient attack technique due to the precision of the results. However, it is also the most expensive because it requires a high-cost laser source and a precise stage to inject light successfully. Both front side and back side access are proven methods used in this technique.
Front side access is harder to break through due to specific physical countermeasures implemented on the metal circuitry itself, which may block the light. Therefore, the vast majority of LFI attacks are carried out through the back side of the chip.
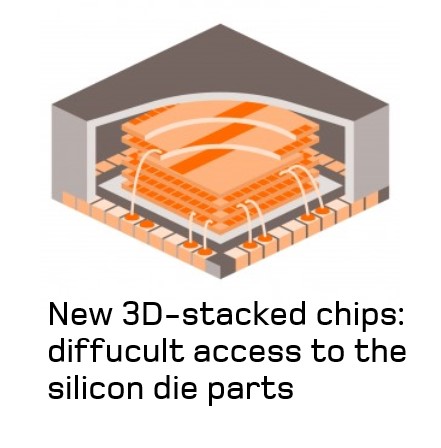
However, back side access is also becoming harder to achieve. In order to improve performance, integration density and costs, developers are starting to integrate chips in three dimensional stacks. These new designs of chips will make it difficult to access the front side and back side surfaces. Furthermore, new physical countermeasures are being developed to protect the IC’s back side against LFI and prevent access to the active area of the silicon die, even when the back side surface of the chip is available.
Lateral Laser Fault Injection: a new variant that widens the surface of attack
As part of our R&D activities, our team conceptualised a new variant of the LFI attack that uses the lateral side of the chip as a new surface of attack to bypass some of the current LFI restrictions.
The experiments conducted at our Cybersecurity laboratory in Barcelona (Spain) demonstrated the effectiveness of Lateral Laser Fault Injection attack (LLFI), especially when 3D-packaging techniques or physical countermeasures constrain back side access. Thanks to the research conducted by Applus+ Laboratories, the LLFI-attack technique adds a new dimension for IT evaluators to consider when conducting the vulnerability analysis of any given chip during the certification process.
To read further about the LLFI attack technique, and the results of the experiment, you can review our white paper ‘
LLFI: Lateral Laser Fault Injection Attack', presented at the FDTC security conference in Atlanta, USA in August. (Authors: Jordi Mujal, Alex Baldomero, Joaquin Rodriguez).
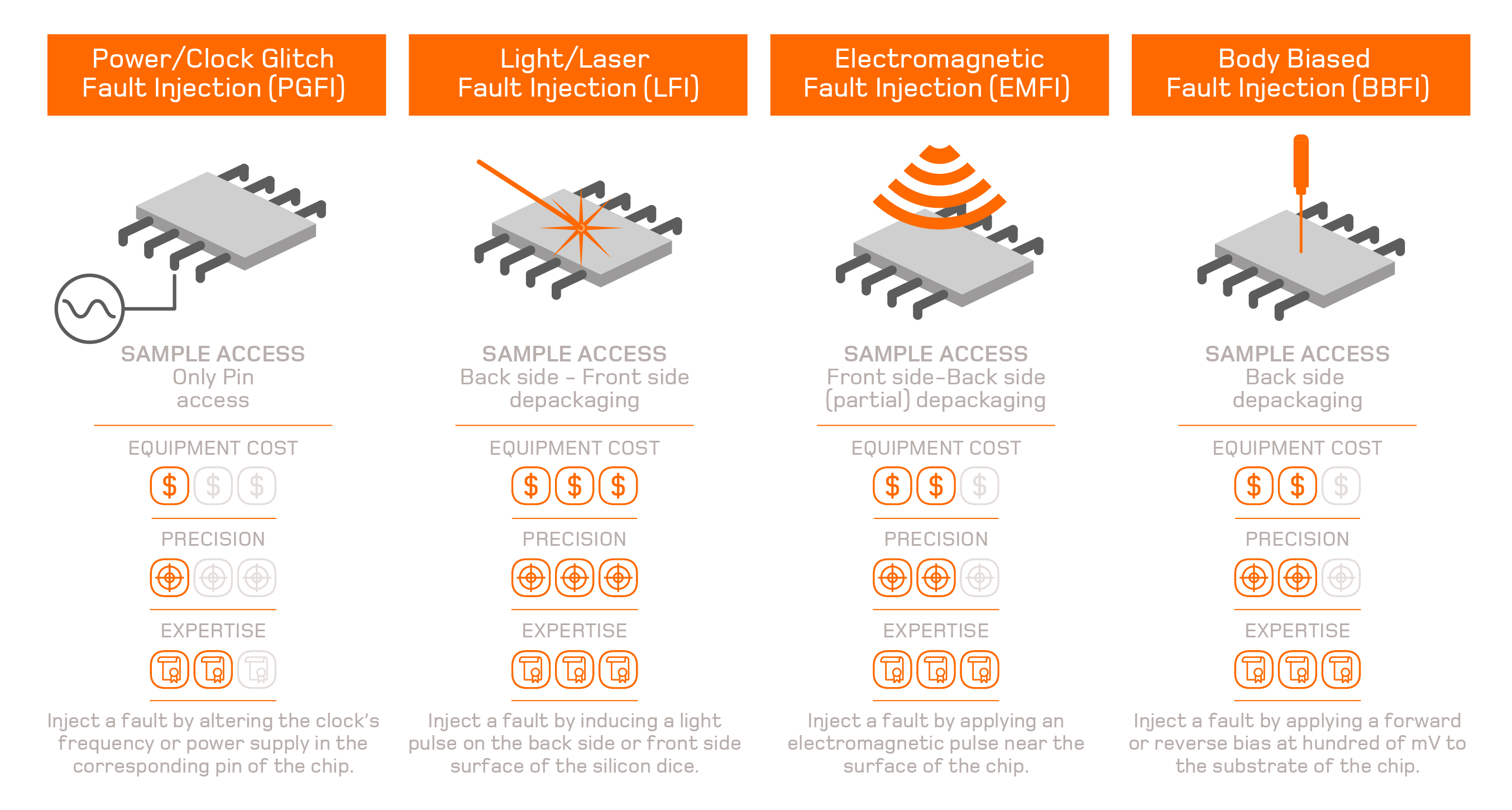
 Laser Fault Injection (LFI) is considered to be the most efficient attack technique due to the precision of the results. However, it is also the most expensive because it requires a high-cost laser source and a precise stage to inject light successfully. Both front side and back side access are proven methods used in this technique.
Laser Fault Injection (LFI) is considered to be the most efficient attack technique due to the precision of the results. However, it is also the most expensive because it requires a high-cost laser source and a precise stage to inject light successfully. Both front side and back side access are proven methods used in this technique.